Introduction
Multi-Factor Authentication (MFA) is an effective way to protect accounts from unauthorized access should an account’s password ever get compromised and is often a vital component of an organization’s security posture to mitigate against an external attacker gaining access to sensitive corporate infrastructure. Organizations can choose to implement MFA through numerous identity providers such as Microsoft, Duo, Okta or other security solutions to require a second factor to verify identity before accessing services such as Microsoft 365 and/or VPNs. However, a common security gap in many MFA implementations is the enrollment process where a user is allowed to enroll in MFA with only a password if they have not previously registered. With this article, I am hoping to describe what this issue is, provide typical examples of the types of users affected, and provide some recommended mitigations to address this security gap.

The Enrollment Gap
Through default or chosen configurations, MFA is commonly implemented by an organization which prompts the user to self-enroll in MFA upon their next login without any additional verifications. Insecure self-enrollment only requires single-factor authentication if you already know the username and password.
Often, during my external network assessments, this enrollment gap is a crucial part of an attack chain that leads to internal or cloud network access. While an organization’s password policy is often the first line of defense against account compromise it is frequently not enough to prevent an external attacker from compromising an account. Social engineering and phishing attacks are common methods for a threat actor to gain initial credentials and I could write another article on the common patterns I have seen that have led to successful password spray attacks, even when 15-character minimums are enforced with complexity requirements. Due to insecure single-factor MFA enrollment, if a compromised account has not yet enrolled, an attacker can register their own device to complete the enrollment process.
Common Types of Unenrolled Users
At this point one might ask what the major concern is regarding this enrollment gap. Shouldn’t the window for an attacker to abuse this gap be small and/or non-existent? Wouldn’t this be an acceptable risk for most organizations as users should be logging in shortly enough after MFA is enforced? Unfortunately for most organizations that might be relying on default MFA configurations, this gap is often larger than what might be presumed as there are several types of accounts that fall under the enrollment gap than an organization might not be considering and/or monitoring.
- Service accounts
- Contractor accounts
- Newly provisioned and/or password reset accounts
Other types of accounts that might be more prone to weak enrollment are on-premises accounts that do not have a mailbox configured. Examples of these type of accounts could be shared organizational accounts for departments and administrative accounts. Organizations not regularly auditing and disabling inactive accounts can also lead to a higher number of users that might be susceptible to weak enrollment. In short, organizations should ensure proper policies are in place to audit the enrollment status of all accounts within the organization. If an account from the above examples is also configured to have Microsoft 365 or VPN access, then insecure enrollment can be used to gain access to sensitive corporate information and potentially the internal network.
I also want to note that while I have occasionally directly compromised an account with insecure enrollment through password spraying and/or credential stuffing from breach data, more often it is the result of a chain of configuration gaps that allows me to target the accounts detailed above after compromising an initial user of an organization. After gaining access to a single valid Active Directory/Microsoft 365 credential, it is often possible to pull verbose information on all domain users due to Microsoft endpoints that do not require MFA to conduct more targeted password spraying attacks to discover weak enrollment accounts. These MFA access gaps are worthy of their own article, similar to insufficient password policies, but the important takeaway is that common and default MFA security configurations relied upon by many organizations lead to real gaps that can allow an attacker with sufficient time and determination to discover and compromise accounts with weak enrollment.
Some Recommendations

While there are several different MFA security solutions, here are some example settings within Microsoft and Duo as reference for potential solutions to address this security gap. If you use a different solution, review the configuration and vendor documentation to ensure the enrollment process is secure.
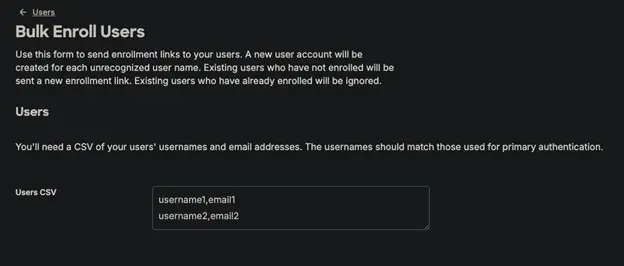
Duo
Microsoft
Unlike Duo, Microsoft services do not allow the option of completely restricting the default self-enrollment but it is possible to associate phone numbers prior to self-enrollment to prevent arbitrary device enrollment. There are some caveats to this approach, as it requires SMS to be the default method for the account and for SMS to be an enabled MFA authentication method.
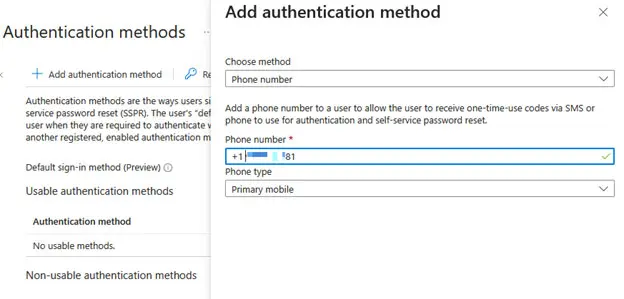
Alternatively, strict conditional access policies within Microsoft could be utilized to restrict logins for any account that has not yet enrolled after implementing an onboarding group that is allow-listed for an appropriate time for enrollment. Further, stricter conditional access policies should limit any login events for any service accounts (and any other accounts that cannot use MFA methods) unless they come from a trusted network. Microsoft also offers Microsoft Entra ID Protection which has automated protections against enrollment and sign-ins for any organizations with Microsoft Entra ID P2 licenses.
Conclusion
Insecure MFA enrollment can be a Catch-22 situation for organizations looking to implement MFA to prevent unauthorized access. Default configurations associated with self-enrollment often only require knowing the username and password to complete enrollment since the equivalent of requiring MFA to enroll in MFA is both a technical and procedural hurdle. Hopefully by highlighting what this issue is, how it can be a real risk to organizations, and some potential solutions, you can reduce the chance of an attacker breaching your external perimeter, accessing sensitive business functions, or gaining an internal foothold.
Joel Coakley is a Senior Offensive Security Consultant with Depth Security, a Konica Minolta Service. With an extensive background in consulting and network and Active Directory testing, Joel is focused on improving his methods on how to best communicate the risks small and enterprise organizations face alike with practical and tangible feedback tailored to each organization’s environment and business needs. Outside of work, Joel enjoys spending time with his wife, family and friends, spoiling his pets, and going on runs in preparation for a marathon. If you’re interested in hiring Depth Security for our Penetration Testing services, please visit our contact page, or email sales@depthsecurity.com.
