Fierce is a simple but very useful DNS reconnaissance tool written by Robert Hansen (RSnake) that I use on virtually every pentest, vuln assessment, or application security assessment I’m involved in. There’s nothing fancy or super-technical about this tool; it’s just useful and deserves some mention. It combines the functionality of a handful of recon tools into one. It’s original purpose was to identify targets for blind pentests for which the address space of the target is not known. However, it’s also great way to enumerate DNS records on targets for which you do know the address space.
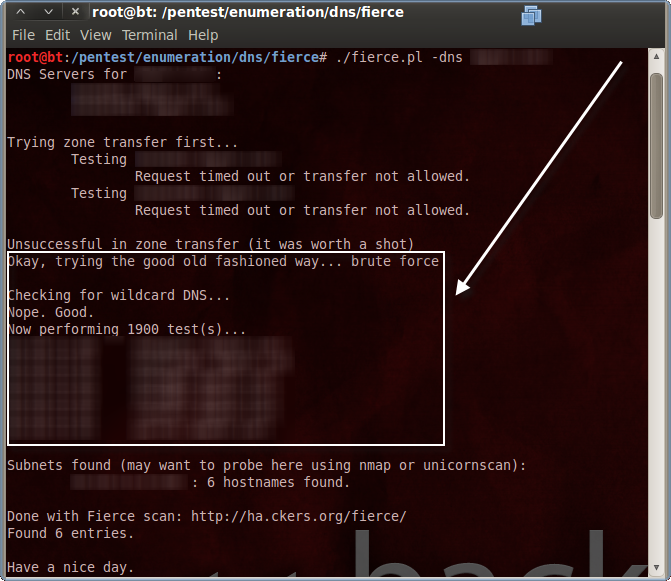
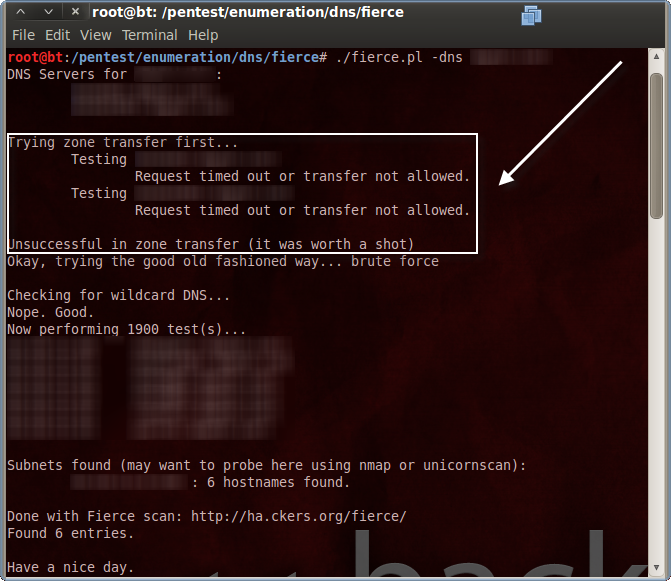
Fierce first identifies authoritative DNS servers for the target domain specified. The next thing it attempts is a zone transfer, or, a dump of all domain records from each authoritative DNS server. While nice (from a pen-tester’s perspective), anonymous DNS zone transfers are rarely allowed these days.
If zone transfer fails then the real usefulness of Fierce becomes apparent. Fierce next brute-force DNS records using a dictionary of common hostnames. This will find DNS records such as www.depthsecurity.com, dev01.depthsecurity.com, cctv.depthsecurity.com and the like. There are other tools that do this but Fierce comes with an already-decent dictionary and does so much more. The real benefit of this, in my opinion, is finding host header names. When multiple, unique websites share the same IP address and port, a port scan will simply identify the single HTTP instance as open. Without the individual websites’ hostnames, a pentester will miss the potentially vulnerable code/content of all those websites.
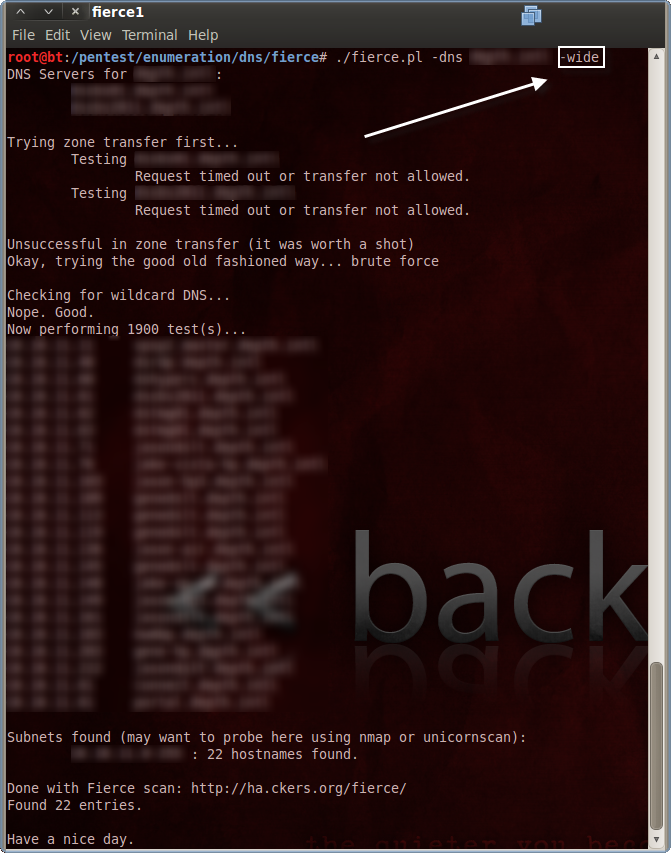
Fierce also has some interesting reverse DNS lookup options. Specifying the “-wide” option will cause Fierce to query PTR records for the entire class C space of any unique /24-bit networks it identifies.
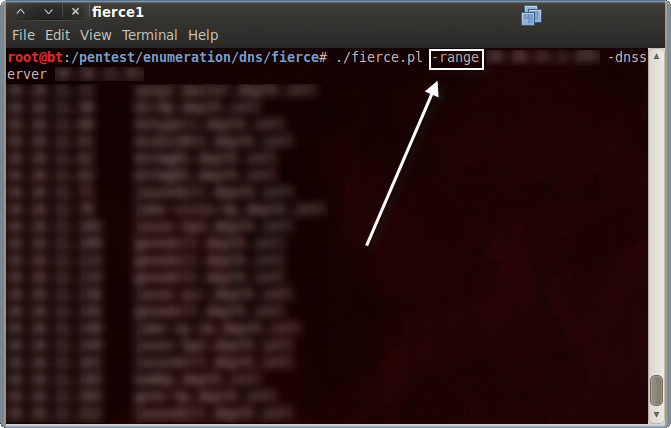
Using the “-range” option along with either the “-dnsserver” or “-dnsfile” will perform reverse lookups for the range specified using the DNS server(s) included.